Architecture
Architecture
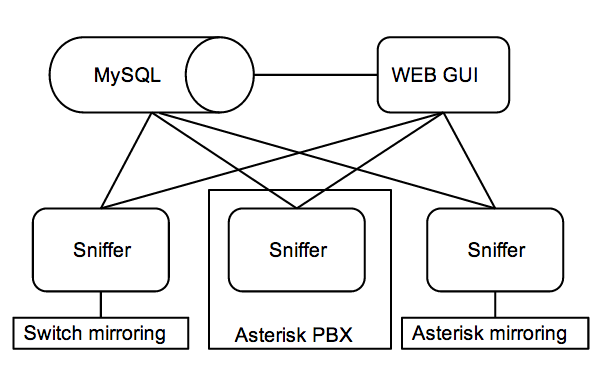
VoIPmonitor architecture allows running multiple sensors (linux) and central MySQL and GUI server. Call detail records (CDR) are send over MySQL TCP protocol to local or remote database and pcap files (SIP and RTP packets) are saved to local sensor storage. WEB GUI reads CDR from database and reads pcap files from local disk (in all in one setup) or directly from the sniffer over TCP manager interface (TCP port 5029).
All in one
If the sensor is installed on the same server as MySQL and GUI you do not need to configure sensors in GUI. The GUI is reading PCAP files directly from local file system and database are connected via localhost mysql database.
Multiple remote sensors one DB/GUI server
Sensors can be configured in two ways - mirroring all packets by the remote sniffer to central sniffer or the remote sniffer is processing VoIP directly and only sends CDR to remote database keeping pcap files on local storage.
Standard remote sniffer
Remote sensor in standard mode processes all packets and stores CDR to database keeping pcap files on local disk. This setup generates minimal traffic between sensor and remote database (it sends only CDR)
What you need to configure on remote sniffer:
- /etc/voipmonitor.conf
id_sensor = unique_number < 65535 managerip = 0.0.0.0
- allow TCP port 5029 on firewall from GUI server
What you need to configure on central GUI
- Go to main menu -> Settings -> Sensors -> add sensor ID, IP, port 5029, keep mysql settings blank.
Mirroring sniffer
Since version 8 remote sensor can be configured as packet sender (mirrorer) to remote sensor which runs on different server. In this mode the sender sends all packets via compressed TCP stream to remote sniffer like it is sniffing directly on network interface. This setup is common in situation where you are not able to mirror packets directly via port spanning or taping and you need to install it directly on linux server where the PBX/SBC runs and you do not have to enough CPU or storage resources to process all packets there - the sender sensor uses minimal CPU / memory resources.
What you need to configure on remote sniffer (for example remote sniffer has IP 10.0.0.1, central sniffer has IP 192.168.0.1)
voipmonitor.conf: interface = eth0 ringbuffer = 200 #up to 2000MB packetbuffer_enable = yes packetbuffer_total_maxheap = 2000 #in MB packetbuffer_compress = yes #enable compression packetbuffer_file_totalmaxsize = 0 #MB. Default is disabled. packetbuffer_file_path = /var/spool/voipmonitor/packetbuffer mirror_destination_ip = 192.168.0.1 mirror_destination_port = 5030
What you need to configure on central sniffer - configure voipmonitor.conf as a standard sniffer + mirror* options :
voipmonitor.conf mirror_bind_ip = 192.168.0.1 mirror_bind_port = 5030 mirror_bind_dlt = 1 // DLT_EN10MB Ethernet (10Mb)
Sniffing packets
VoIPmonitor sniffer can run only on Linux. You can compile it or download static binaries and run it directly on your PBX / SBC. But although the sniffer was designed to handle thousands of simultaneous calls it is recommended to install it on dedicated Linux server (which can be also virtual).
Mirroring packets
Hardware mirroring
If the sniffer cannot run directly on PBX/SBC you need to mirror packets to sniffer server. The most common approach is to do it in hardware switch. This feature is called spanning / mirroring / taping ports. Check if your switch can do this. Some PBX/SBC are capable of mirroring packets using IP in IP protocol which voipmonitor supports natively (enabled by default).
Software mirroring
If your switch lacks mirroring feature you can mirror packets using mirror function in the sniffer. Refer to the sniffer manual section.