Ribbon7k monitoring profiles: Difference between revisions
(Clarify HA failover handling - remove only ribbonsbc_srcip, keep dstip/port for filtering) |
(Patch: replace '# Transport & framing options:...') |
||
| (4 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= | = Ribbon SBC Monitoring Profile for VoIPmonitor = | ||
This page explains how to use the Ribbon SBC '''Monitoring Profile''' to export TLS-decrypted SIP signaling to a VoIPmonitor server. | |||
On the SBC navigate to All > Profiles > Services > Monitoring Profile. The Monitoring Profile window displays, containing the table Monitoring Profile List. | == Overview == | ||
The Ribbon SBC can decrypt TLS/SRTP traffic internally and forward clear-text SIP to VoIPmonitor, eliminating the need for SSL key loggers when dealing with TLS 1.3 or PFS cipher suites (DHE/ECDHE). | |||
<kroki lang="mermaid"> | |||
%%{init: {'flowchart': {'nodeSpacing': 15, 'rankSpacing': 40}}}%% | |||
flowchart LR | |||
subgraph TLS["TLS Encrypted"] | |||
EP[Phone/Endpoint] | |||
end | |||
subgraph SBC["Ribbon SBC"] | |||
DEC[TLS Termination] | |||
MP[Monitoring Profile] | |||
end | |||
subgraph VM["VoIPmonitor"] | |||
SNIFF[Sensor] | |||
end | |||
EP -->|"TLS SIP"| DEC | |||
DEC -->|"Decrypt"| MP | |||
MP -->|"Clear SIP<br/>Port 9514"| SNIFF | |||
</kroki> | |||
{{Note|1='''Ribbon SBC''' (Ribbon Communications, formed from GENBAND + Sonus Networks merger in 2017) is a '''different vendor''' than '''Oracle SBC''' (formerly Acme Packet). They use different protocols: | |||
* '''Ribbon SBC''' → Monitoring Profile with <code>ribbonsbc</code> parameters (this page) | |||
* '''Oracle SBC''' → IPFIX protocol with <code>ipfix</code> parameters (see [[Sniffer_configuration#IPFIX_Support|IPFIX Support]]) | |||
}} | |||
== Configuring the Monitoring Profile == | |||
To export TLS-decrypted signaling from the Ribbon SBC, use the Monitoring Profile feature. | |||
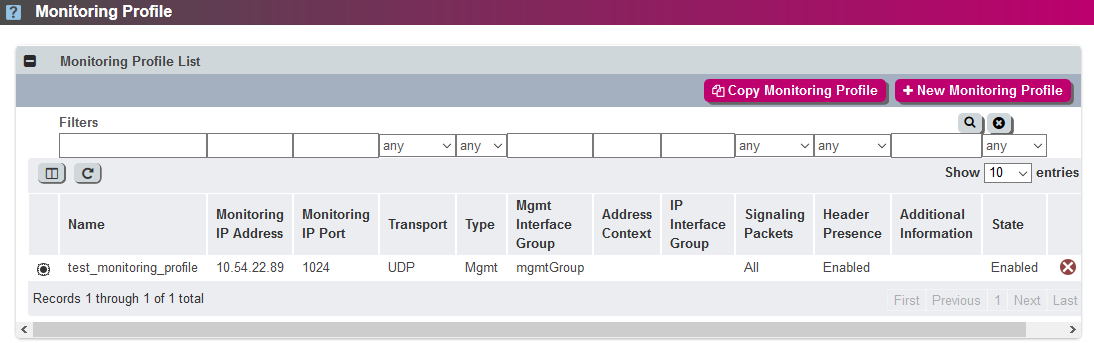
On the SBC navigate to '''All > Profiles > Services > Monitoring Profile'''. The Monitoring Profile window displays, containing the table Monitoring Profile List. | |||
[[File:Ribbon_tls_monitProfile.png]] | [[File:Ribbon_tls_monitProfile.png]] | ||
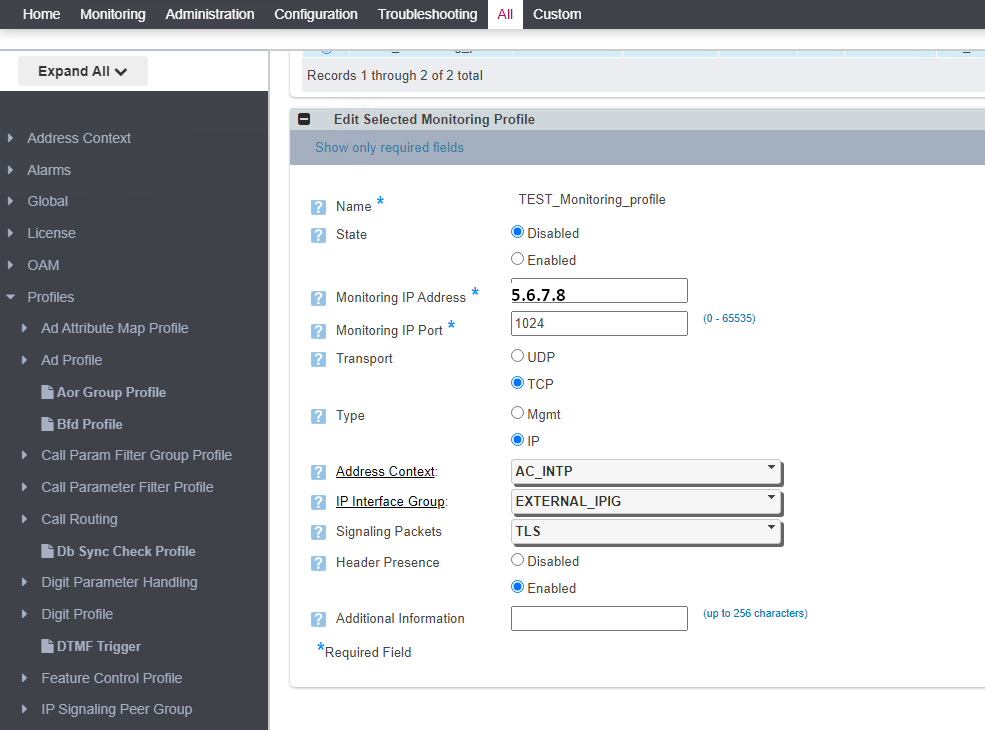
Modify the monitoring profile to send only TLS signaling to the remote server: | Modify the monitoring profile to send only TLS signaling to the remote server: | ||
| Line 13: | Line 40: | ||
[[File:Ribbon_tls_ProfileEdit.png]] | [[File:Ribbon_tls_ProfileEdit.png]] | ||
== Assigning the Monitoring Profile to a SIP Signaling Port == | |||
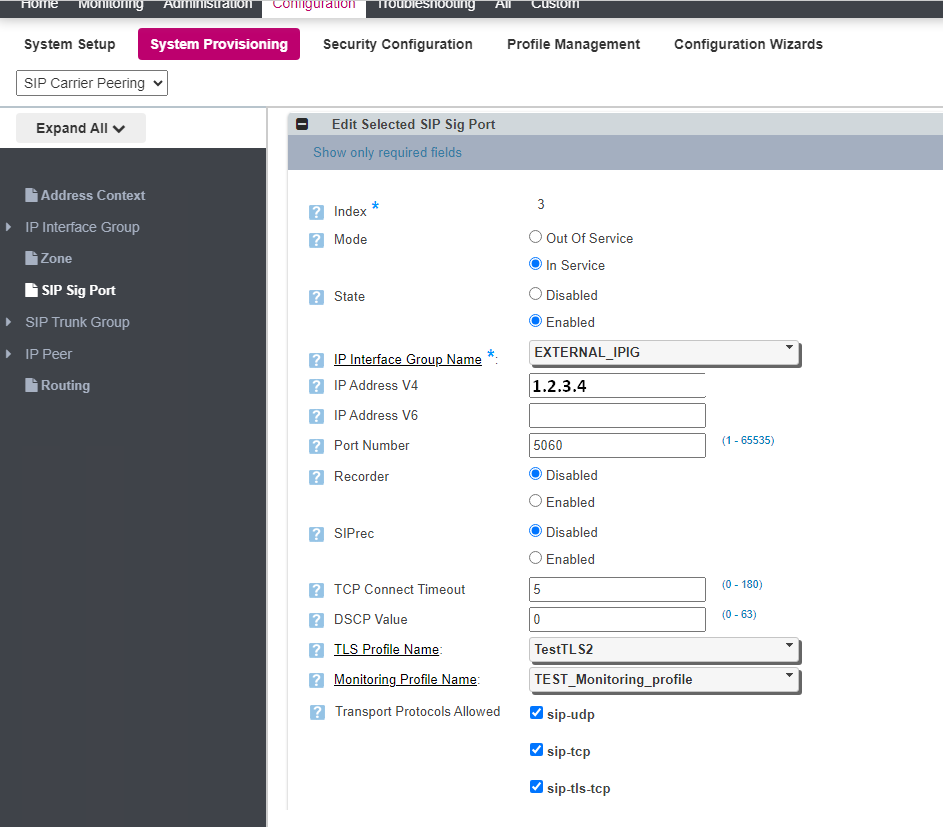
Execute the following CLI command on the Ribbon host: | |||
<syntaxhighlight lang="bash"> | |||
set addressContext AC_INTP zone INTERNAL_IPIG sipSigPort 1 monitoringProfileName TEST_Monitoring_Profile | |||
</syntaxhighlight> | |||
The syntax: | The syntax: | ||
<syntaxhighlight lang="bash"> | |||
set addressContext <address_context> zone <zone_name> sipSigPort 1 monitoringProfileName <monitoring_profile_name> | |||
</syntaxhighlight> | |||
[[File:Ribbon_tls_assignMonitProfile.png]] | |||
== Incorporating Source and Destination IPs == | |||
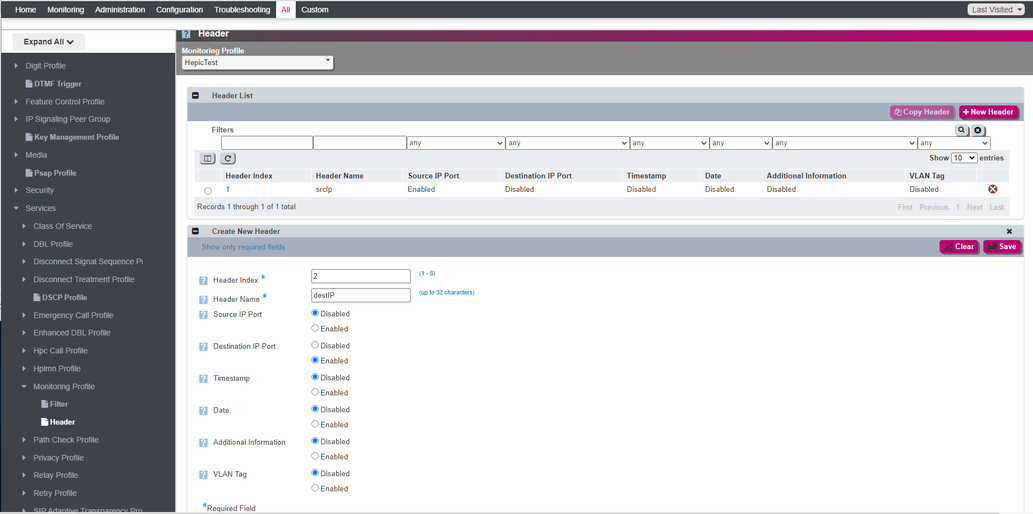
You may also need the source and destination IPs incorporated in the feed to the monitoring server. Under '''Header''' add the source and destination IPs to the selected monitoring profile. | |||
[[File:Ribbon_tls_incorporatingIPs.png]] | |||
This gets the source and destination IPs incorporated in the SIP signaling sent to the remote server. From here the data can be ingested and processed by the far end server. | |||
'''Reference:''' [https://doc.rbbn.com/display/SBXDOC121/Services+-+Monitoring+Profile Ribbon's official documentation] | |||
== VoIPmonitor Configuration == | |||
VoIPmonitor supports two modes for receiving Ribbon monitoring data: | |||
{| class="wikitable" | |||
|- | |||
! Mode !! Description !! When to Use | |||
|- | |||
| '''Passive Sniffing''' || Substitutes src/dst IP:port in already sniffed traffic || Traffic arrives via SPAN/mirror | |||
|- | |||
| '''Active Listener''' || Opens a socket to receive Ribbon feed directly || Direct TCP/UDP connection from SBC | |||
|} | |||
=== Mode 1: Passive Sniffing === | |||
Add to <code>/etc/voipmonitor.conf</code>: | |||
<syntaxhighlight lang="ini"> | |||
# Enable Ribbon-style IP substitution on sniffed traffic | |||
ribbonsbc = yes | |||
# Optional filters (legacy but still supported): | |||
# ribbonsbc_port = 9514 # expected mirror port | |||
# ribbonsbc_dstip = 10.0.0.1 # VoIPmonitor host IP | |||
# ribbonsbc_srcip = 10.0.0.2 # Ribbon SBC IP | |||
</syntaxhighlight> | |||
= | {{Warning|1=For '''High Availability (HA) setups''', do NOT use <code>ribbonsbc_srcip</code> - it will fail when traffic originates from a different SBC node after failover. Use only <code>ribbonsbc_port</code> and <code>ribbonsbc_dstip</code>.}} | ||
= | === Mode 2: Active Listener === | ||
Add to <code>/etc/voipmonitor.conf</code>: | |||
<syntaxhighlight lang="ini"> | |||
# Listen for Ribbon monitoring data | |||
ribbonsbc_bind_ip = 0.0.0.0 | |||
ribbonsbc_bind_port = 9514 | |||
# Framing options: | |||
# ribbonsbc_size_header = yes # expect 2-byte size header (default) | |||
# ribbonsbc_strict_check = no # drop incomplete frames | |||
# ribbonsbc_counter_log = no # log incoming frame counts | |||
# Note: TCP+UDP automatically bound since 2026.1.3 | |||
</syntaxhighlight> | |||
= | After configuration, restart the service: | ||
<syntaxhighlight lang="bash"> | |||
systemctl restart voipmonitor | |||
</syntaxhighlight> | |||
== Verification == | |||
=== Verify on the SBC === | |||
Verify on the SBC that the data are traveling to the remote server: | |||
= | <syntaxhighlight lang="bash"> | ||
tshark -i pkt1 port 9514 | |||
</syntaxhighlight> | |||
=== Verify on the Monitoring Server === | |||
Verify that the packets are arriving from SBC: | |||
<syntaxhighlight lang="bash"> | |||
tcpdump -i any port 9514 -w /var/tmp/capture_from_ribbon.pcap | |||
</syntaxhighlight> | |||
== AI Summary for RAG == | == AI Summary for RAG == | ||
''' | '''Summary:''' Guide for configuring Ribbon SBC Monitoring Profile to export TLS-decrypted SIP signaling to VoIPmonitor. Setup requires: (1) Configure Monitoring Profile in SBC GUI (All > Profiles > Services > Monitoring Profile), (2) Assign profile to SIP port via CLI: <code>set addressContext <AC> zone <ZONE> sipSigPort 1 monitoringProfileName <PROFILE></code>, (3) Add Source/Destination IPs in Header section for proper remapping. VoIPmonitor supports two modes: Passive sniffing (<code>ribbonsbc=yes</code>) for SPAN/mirror traffic, and Active listener (<code>ribbonsbc_bind_ip/port</code>) for direct TCP connection. For HA/failover setups, omit <code>ribbonsbc_srcip</code> filter to accept traffic from any SBC node. Default port is 9514. Verification via tshark on SBC and tcpdump on monitoring server. | ||
'''Keywords:''' Ribbon SBC, Monitoring Profile, TLS decryption, ribbonsbc, passive sniffing, active listener, port 9514, HA failover, IP substitution, SIP signaling | |||
'''Key Questions:''' | '''Key Questions:''' | ||
* How do I configure Ribbon SBC to export TLS-decrypted SIP to VoIPmonitor? | |||
* How do I configure | * What is the CLI command to assign a monitoring profile to a SIP port? | ||
* | * What is the difference between passive sniffing and active listener modes? | ||
* | * How do I configure VoIPmonitor for Ribbon SBC in High Availability (HA) setups? | ||
* Why does ribbonsbc_srcip fail in HA failover scenarios? | |||
* How do I verify traffic is being sent from Ribbon SBC to VoIPmonitor? | |||
* What is the default port for Ribbon monitoring profile (9514)? | |||
* How do I configure VoIPmonitor for | |||
* Why does ribbonsbc_srcip fail in HA | |||
* | |||
Latest revision as of 17:38, 22 January 2026
Ribbon SBC Monitoring Profile for VoIPmonitor
This page explains how to use the Ribbon SBC Monitoring Profile to export TLS-decrypted SIP signaling to a VoIPmonitor server.
Overview
The Ribbon SBC can decrypt TLS/SRTP traffic internally and forward clear-text SIP to VoIPmonitor, eliminating the need for SSL key loggers when dealing with TLS 1.3 or PFS cipher suites (DHE/ECDHE).
ℹ️ Note: Ribbon SBC (Ribbon Communications, formed from GENBAND + Sonus Networks merger in 2017) is a different vendor than Oracle SBC (formerly Acme Packet). They use different protocols:
- Ribbon SBC → Monitoring Profile with
ribbonsbcparameters (this page) - Oracle SBC → IPFIX protocol with
ipfixparameters (see IPFIX Support)
Configuring the Monitoring Profile
To export TLS-decrypted signaling from the Ribbon SBC, use the Monitoring Profile feature.
On the SBC navigate to All > Profiles > Services > Monitoring Profile. The Monitoring Profile window displays, containing the table Monitoring Profile List.
Modify the monitoring profile to send only TLS signaling to the remote server:
Assigning the Monitoring Profile to a SIP Signaling Port
Execute the following CLI command on the Ribbon host:
set addressContext AC_INTP zone INTERNAL_IPIG sipSigPort 1 monitoringProfileName TEST_Monitoring_Profile
The syntax:
set addressContext <address_context> zone <zone_name> sipSigPort 1 monitoringProfileName <monitoring_profile_name>
Incorporating Source and Destination IPs
You may also need the source and destination IPs incorporated in the feed to the monitoring server. Under Header add the source and destination IPs to the selected monitoring profile.
This gets the source and destination IPs incorporated in the SIP signaling sent to the remote server. From here the data can be ingested and processed by the far end server.
Reference: Ribbon's official documentation
VoIPmonitor Configuration
VoIPmonitor supports two modes for receiving Ribbon monitoring data:
| Mode | Description | When to Use |
|---|---|---|
| Passive Sniffing | Substitutes src/dst IP:port in already sniffed traffic | Traffic arrives via SPAN/mirror |
| Active Listener | Opens a socket to receive Ribbon feed directly | Direct TCP/UDP connection from SBC |
Mode 1: Passive Sniffing
Add to /etc/voipmonitor.conf:
# Enable Ribbon-style IP substitution on sniffed traffic
ribbonsbc = yes
# Optional filters (legacy but still supported):
# ribbonsbc_port = 9514 # expected mirror port
# ribbonsbc_dstip = 10.0.0.1 # VoIPmonitor host IP
# ribbonsbc_srcip = 10.0.0.2 # Ribbon SBC IP
⚠️ Warning: For High Availability (HA) setups, do NOT use ribbonsbc_srcip - it will fail when traffic originates from a different SBC node after failover. Use only ribbonsbc_port and ribbonsbc_dstip.
Mode 2: Active Listener
Add to /etc/voipmonitor.conf:
# Listen for Ribbon monitoring data
ribbonsbc_bind_ip = 0.0.0.0
ribbonsbc_bind_port = 9514
# Framing options:
# ribbonsbc_size_header = yes # expect 2-byte size header (default)
# ribbonsbc_strict_check = no # drop incomplete frames
# ribbonsbc_counter_log = no # log incoming frame counts
# Note: TCP+UDP automatically bound since 2026.1.3
After configuration, restart the service:
systemctl restart voipmonitor
Verification
Verify on the SBC
Verify on the SBC that the data are traveling to the remote server:
tshark -i pkt1 port 9514
Verify on the Monitoring Server
Verify that the packets are arriving from SBC:
tcpdump -i any port 9514 -w /var/tmp/capture_from_ribbon.pcap
AI Summary for RAG
Summary: Guide for configuring Ribbon SBC Monitoring Profile to export TLS-decrypted SIP signaling to VoIPmonitor. Setup requires: (1) Configure Monitoring Profile in SBC GUI (All > Profiles > Services > Monitoring Profile), (2) Assign profile to SIP port via CLI: set addressContext <AC> zone <ZONE> sipSigPort 1 monitoringProfileName <PROFILE>, (3) Add Source/Destination IPs in Header section for proper remapping. VoIPmonitor supports two modes: Passive sniffing (ribbonsbc=yes) for SPAN/mirror traffic, and Active listener (ribbonsbc_bind_ip/port) for direct TCP connection. For HA/failover setups, omit ribbonsbc_srcip filter to accept traffic from any SBC node. Default port is 9514. Verification via tshark on SBC and tcpdump on monitoring server.
Keywords: Ribbon SBC, Monitoring Profile, TLS decryption, ribbonsbc, passive sniffing, active listener, port 9514, HA failover, IP substitution, SIP signaling
Key Questions:
- How do I configure Ribbon SBC to export TLS-decrypted SIP to VoIPmonitor?
- What is the CLI command to assign a monitoring profile to a SIP port?
- What is the difference between passive sniffing and active listener modes?
- How do I configure VoIPmonitor for Ribbon SBC in High Availability (HA) setups?
- Why does ribbonsbc_srcip fail in HA failover scenarios?
- How do I verify traffic is being sent from Ribbon SBC to VoIPmonitor?
- What is the default port for Ribbon monitoring profile (9514)?