Ribbon7k monitoring profiles
Use the monitoring profile
For getting the TLS signalling decrypted by ribbon SBC:
We will use the Monitoring Profile feature to send only TLS decoded signaling to a voipmonitor server
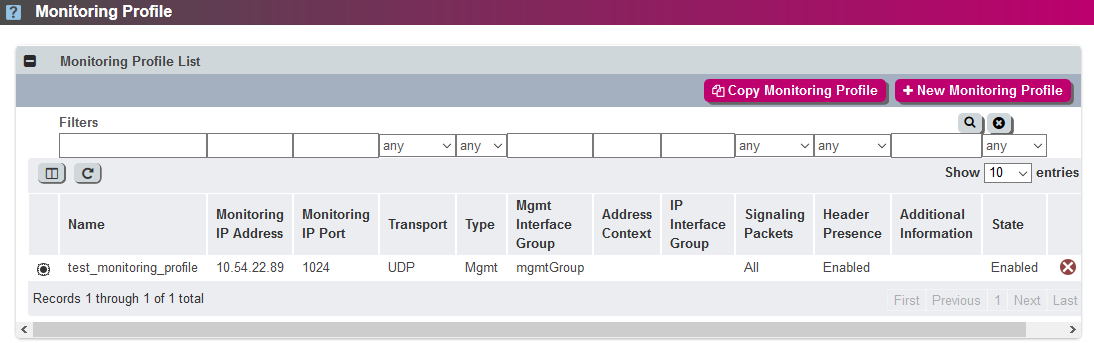
On the SBC navigate to All > Profiles > Services > Monitoring Profile. The Monitoring Profile window displays, containing the table Monitoring Profile List.
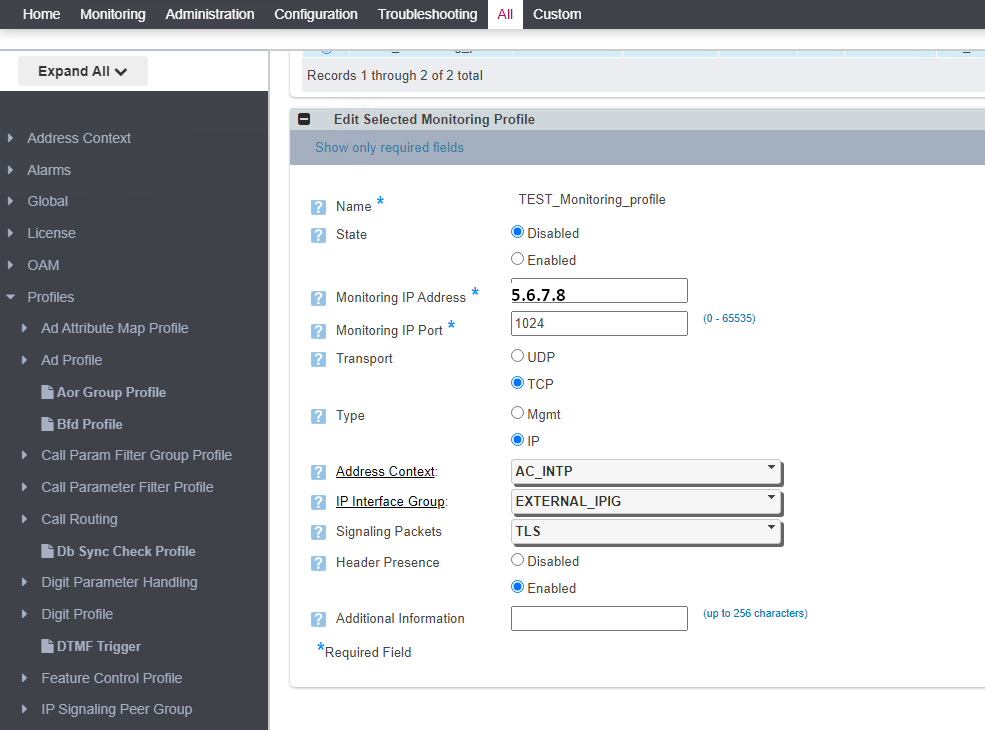
Modify the monitoring profile to send only TLS signaling to the remote server:
Execute the following CLI command (on Ribbon host)
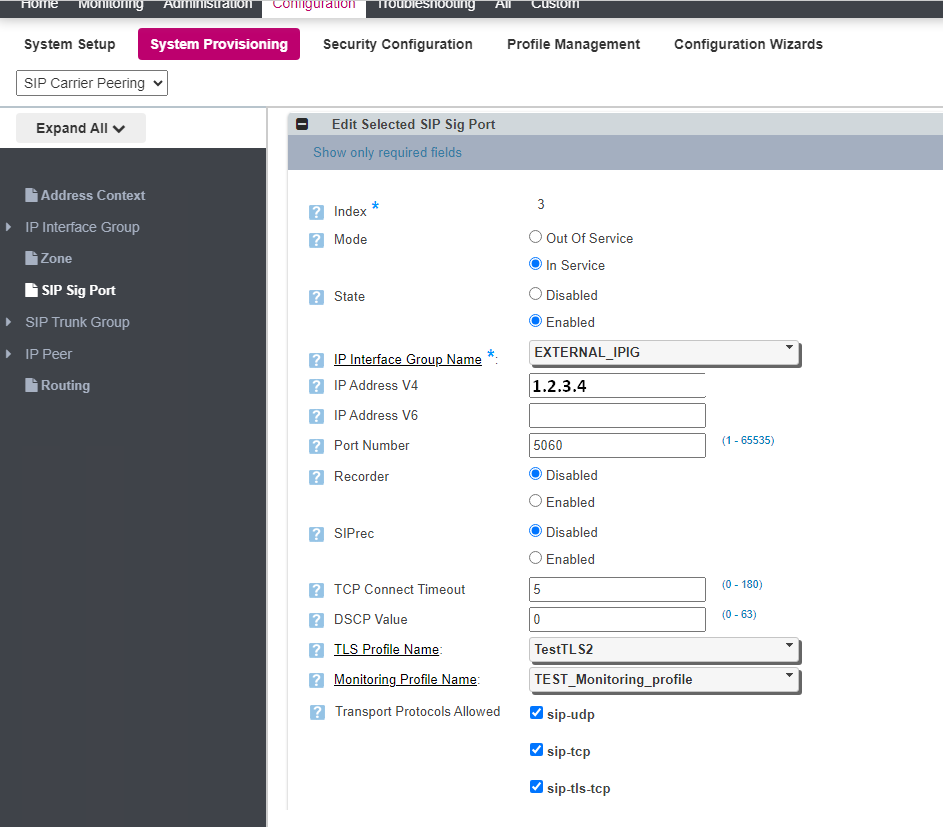
set addressContext AC_INTP zone INTERNAL_IPIG sipSigPort 1 monitoringProfileName TEST_Monitoring_Profile
The syntax:
set addressContext <address_context> zone <zone_name> sipSigPort 1 monitoringProfileName <monitoring_profile_name>
Verify that SBC are sending data
Verify on the SBC that the data are traveling to the remote server:
tshark -i pkt1 port 9514
Assign the TEST_Monitoring_Profile to the Sip Signaling Port
Verify on the monitoring server
that the packets are arriving from sbc:
tcpdump -i any port 9514 -w /var/tmp/Capture_Mar26_fromRibbon_TLS_only.pcap
Incorporating source and dest IP with monitoring profile
You may also need the source and destination IPs incorporated in the feed to the monitoring server. Under Header add the source and destination IPs to the selected monitoring profile.
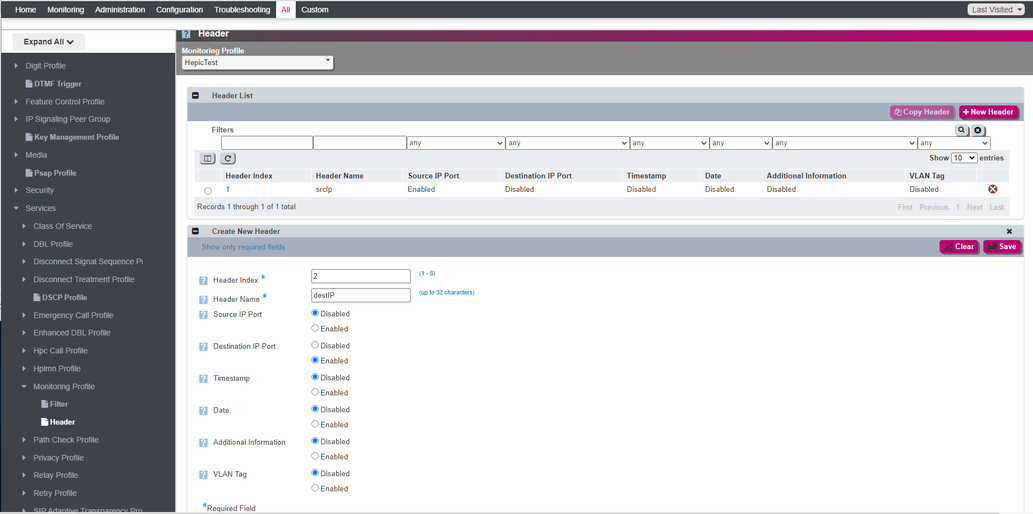
This gets the source and destination IPs incorporated in the SIP signaling sent to the remote server. From here the data can be injested and processed by the far end server. The packets appear as follows on the far end server.
The source: Ribbon's site at https://doc.rbbn.com/display/SBXDOC121/Services+-+Monitoring+Profile
VoIPmonitor.conf
##################################### # Ribbon SBC Mirroring / ribbonsvc # ##################################### # This module handles Ribbon SBC "monitoring profile" mirrored SIP/RTP data. # It supports two modes: # 1) Passive sniffing – substitute src/dst IP:port in already sniffed traffic # 2) Active listener – accept Ribbon "monitoring profile" feed on a local socket # # It is similar to "Kamailio Mirroring using siptrace", but uses a minimal header set. ########### # MODE 1: PASSIVE SNIFFING (no socket opened) # # Quick enable: # ribbonsbc = yes # When enabled, VoIPmonitor will try to detect and apply IP:port substitutions # if substitution content is present in sniffed packets. # # Optional narrowing (legacy but still supported): # Use the triplet below to restrict which mirrored packets should be considered. # Keep using this if you need explicit filtering; otherwise just set ribbonsbc = yes. # # ribbonsbc_port = 9514 # expected mirror port seen in packets (legacy filter) # ribbonsbc_dstip = 10.0.0.1 # VoIPmonitor host IP as seen by Ribbon (legacy filter) # ribbonsbc_srcip = 10.0.0.2 # Ribbon SBC IP (legacy filter) # # Note: If 'ribbonsbc' is enabled (yes/NO), substitution is attempted whenever # substitution content is found. Same idea applies to 'kamailio' (see below). ########### # MODE 2: ACTIVE LISTENER (open a socket and ingest feed directly) # # Bind an explicit local IP/port to receive Ribbon monitoring data. If these are set, # the sniffer will listen and process incoming Ribbon data on this socket. # # ribbonsbc_bind_ip = 0.0.0.0 # listen address (required to enable active mode) # ribbonsbc_bind_port = 9514 # listen port (required to enable active mode) # # Transport & framing: # ribbonsbc_bind_udp = no # yes/NO – UDP support (default NO; TCP recommended) # ribbonsbc_size_header = YES # YES/no – expect 2-byte size header before each frame # ribbonsbc_strict_check= no # yes/NO – process only frames complete per size header # # Instrumentation: # ribbonsbc_counter_log = no # yes/NO – log counts of incoming Ribbon frames # # TIP: Active listener generally makes sense with TCP (default). UDP is rarely useful. ########### # SUBSTITUTION SWITCHES (shared idea with Kamailio) # # These switches only control whether src/dst IP:port substitution is attempted in # normally sniffed traffic when substitution content is present. If enabled and # a substitution block is detected, it is applied without having to predeclare # specific IP:ports (unlike the legacy triplet). # # kamailio = no # yes/NO – enable Kamailio-style substitution on sniffed traffic # ribbonsbc = yes # yes/NO – enable Ribbon-style substitution on sniffed traffic ########### # RECOMMENDATIONS # # - Use MODE 1 (passive) with: ribbonsbc = yes # Only add ribbonsbc_port/dstip/srcip if you need strict filtering by IP/port. # # - Use MODE 2 (active) when Ribbon sends the monitoring profile feed directly to you: # ribbonsbc_bind_ip = 0.0.0.0 # ribbonsbc_bind_port = 9514 # Keep ribbonsbc_bind_udp = no unless you explicitly need UDP. # # - Leave ribbonsbc_size_header = YES unless you know Ribbon is sending raw frames. # - Enable ribbonsbc_strict_check = yes if you want to drop any incomplete frames. # # DEFAULTS (implicit unless set): # ribbonsbc = no # kamailio = no # ribbonsbc_bind_udp = no # ribbonsbc_size_header = YES # ribbonsbc_strict_check = no # ribbonsbc_counter_log = no
AI Summary for RAG
Summary: This page explains how to use the Ribbon SBC Monitoring Profile to export TLS-decrypted SIP signaling to a VoIPmonitor server. It covers where to configure the monitoring profile in the SBC GUI, how to assign it to a specific SIP signaling port (including the required CLI syntax), and how to verify traffic both on the SBC (tshark on the capture interface) and on the monitoring server (tcpdump on port 9514). It also shows how to embed source and destination IPs into the exported feed by adding headers in the monitoring profile, so the far end (VoIPmonitor) can reliably remap/ingest the traffic. The page includes a ready-to-use voipmonitor.conf block for the ribbonsvc integration, describing two modes: (1) Passive sniffing – only IP:port substitution on already sniffed packets; and (2) Active listener – the sensor opens a socket and listens for the Ribbon feed. Advanced options include TCP/UDP selection (TCP recommended), size-header framing, strict frame completeness checks, and optional counters logging.
Keywords: Ribbon SBC, Monitoring Profile, TLS decryption, SIP signaling, VoIPmonitor, ribbonsvc, passive sniffing, active listener, size header, TCP, UDP, src/dst IP substitution, verification, tshark, tcpdump, port 9514
Key Questions:
- How do I configure a Ribbon Monitoring Profile to export only TLS-decrypted SIP signaling?
- How do I assign the monitoring profile to a SIP signaling port (GUI and CLI)?
- How can I verify that the SBC is sending the feed and that the monitoring server is receiving it?
- How do I include src/dst IPs in the exported signaling so VoIPmonitor can substitute addresses?
- When should I use Passive sniffing (substitution only) vs Active listener (open socket) in ribbonsvc?
- Which ribbonsvc options control transport (TCP/UDP), framing (size header), and strict completeness checks?
- What are sensible defaults and recommended settings for reliable ingestion on VoIPmonitor?